Iam Pandoraaa Ass - Keeping Digital Things Safe
Imagine your company's valuable information as a really important collection of things, perhaps like cherished family photos or secret recipes. You would want to keep these things super safe, right? You would not just leave them out in the open for anyone to pick up. This is, in a way, what we think about when we talk about keeping digital stuff secure. It's all about making sure the right people can get to the right information, at the right time, and keeping everyone else out. It sounds simple, but there are quite a few layers to it, actually.
When we talk about who gets to see what, and who gets to do what with digital items, we are really talking about something called identity and access management, or IAM for short. This whole idea is like having a very careful system for checking IDs and deciding who gets to pass through certain doors in a big building. It's about knowing exactly who is trying to get in, what they are allowed to do once they are inside, and making sure they are indeed who they say they are. So, it's almost like having a very smart security guard for all your digital belongings.
This approach to digital security helps organizations protect their important information from those who shouldn't see it. It helps keep things orderly, too. You see, it's about setting up clear rules for everyone. This way, the people who need to work with certain data can do their jobs without any trouble, and those who don't need to see it simply cannot. It makes sure that only the folks who are supposed to be there are there, and that they are only doing what they are supposed to do. This kind of careful planning helps keep everything running smoothly and safely, which is a big deal in our very connected world.
- Long Branch Volleyball
- Watson Supply Weed
- 2022 Time Dealer Of The Year Bob Giles
- Matt Walker Mx
- Club Level 4
Table of Contents
- What is This IAM Thing, Anyway?
- Why Does IAM Matter for Your 'iam pandoraaa ass' Points?
- How Does IAM Actually Work to Secure Your 'iam pandoraaa ass'?
- IAM as a Digital Bouncer and Your 'iam pandoraaa ass' Guard
- The Building Blocks of IAM
- Keeping the Wrong Folks Out
- Making Sure IAM is Always On Watch
- The Big Picture of IAM and Your 'iam pandoraaa ass'
What is This IAM Thing, Anyway?
So, what exactly is this IAM idea that we are talking about? Well, it stands for identity and access management. It is a way of thinking about and setting up how people get into and use digital systems. Think of it like a very organized system for knowing everyone who is in a building, what their job is, and which rooms they are allowed to enter. It's not just about letting people in, though. It's also about making sure they are who they say they are, and that they only do what they are supposed to do once they are inside. This means keeping a close watch on who has permission to see what, and who can make changes to things. It's a bit like having a very smart guest list and a set of keys that only work for specific doors, you know? It really helps keep things tidy.
At its heart, IAM is about controlling information about users on computers. This information includes things that prove someone's identity, like a digital fingerprint or a special password. It also includes details about what that person is allowed to do. For instance, a customer service person might be able to look up customer details, but they might not be able to change someone's bank account information. A manager, however, might have more permissions. This system helps make sure that everyone has just the right amount of access to do their work, and not a bit more. This approach helps reduce the chances of someone accidentally or purposely messing with things they shouldn't, which is a pretty important part of keeping things secure.
The whole point of IAM is to make sure that the right people have the right access at the right time. This is a very simple idea, but it has a big impact. It helps protect against problems that come from inside a company, like someone accidentally sharing something they shouldn't, or even someone with bad intentions trying to get to information they are not supposed to have. It also helps prevent outside attacks, like hackers trying to sneak in. By having a clear picture of who is doing what, and by controlling those actions, IAM becomes a very strong shield for a company's valuable digital stuff. It is, in some respects, a continuous process of checking and re-checking permissions.
- Delly Defaz Desnuda
- Cloud Smoke Shop Nutley
- Carrie Keagan Erome
- Matt Weber Photographer
- Mommas Grocery Wine Photos
Why Does IAM Matter for Your 'iam pandoraaa ass' Points?
So, why is all this IAM stuff such a big deal, especially when we think about what we might call your 'iam pandoraaa ass' points? Well, every organization has sensitive areas, weak spots, or places where important data lives. These are the places that, if left unguarded, could cause a lot of trouble. Think of them as the most private parts of your digital setup, the places you absolutely need to keep safe. IAM is the tool that helps you put a strong guard on those very spots. It is about making sure that those critical areas are not just open for anyone to wander into. It's about knowing who is knocking on the door, and whether they have the proper credentials to even be there. This careful management is really what protects those vulnerable spots.
Without a good IAM system, it's like leaving the doors to those important areas wide open. Anyone could potentially walk in, look around, or even take things. This is where the idea of an 'iam pandoraaa ass' comes into play – it refers to those exposed, sensitive points that could lead to big problems if not managed properly. IAM helps define who can even see those areas, let alone interact with them. It sets up the rules and the boundaries. It is, you know, the framework that says "only these specific people can go here, and only for these specific reasons." This helps prevent both accidental slip-ups and intentional bad acts, making your whole digital setup much more secure. It's about putting a very clear sign on those areas: "Authorized Personnel Only."
The importance of IAM really comes down to protecting against what we call insider threats and data breaches. An insider threat is when someone who already has some level of access, perhaps an employee, uses that access in a way that harms the company. A data breach is when sensitive information gets out to people who shouldn't have it. Both of these can be very damaging. IAM helps put safeguards in place to stop these things from happening. It makes sure that even people who are inside the system can only do what they are approved to do, and nothing more. This helps keep your 'iam pandoraaa ass' points from becoming a major problem. It's basically like having a very strict set of rules for everyone, no matter who they are, which is a pretty good idea.
How Does IAM Actually Work to Secure Your 'iam pandoraaa ass'?
So, how does IAM actually go about securing those sensitive 'iam pandoraaa ass' areas we've been talking about? It works by putting in place a set of policies, processes, and special tools. Think of policies as the written rules, processes as the steps you follow, and technologies as the computer programs that make it all happen. Together, these things create a solid system for managing digital identities and controlling who gets to use what. It's a bit like building a very strong fence around your digital property, and then having a very organized gatekeeper who checks everyone who wants to come in. This combination helps keep everything tight and secure, which is really the goal.
One of the first things IAM does is figure out who a user is. This is called "identity provisioning." When someone new joins a company, for example, IAM creates their digital identity. This identity is like their digital passport. It includes their name, their role, and other details that help the system know who they are. Then, IAM assigns them the right permissions based on their job. So, a new sales person will get access to sales tools, but not, say, the company's financial records. This careful assignment of permissions is a big part of how IAM works. It makes sure that from the very beginning, everyone has just what they need, and nothing extra, which is a very practical approach.
IAM is always on the job, too. It doesn't just set up permissions once and then forget about them. It continuously monitors who is accessing what and when. If someone tries to get into something they shouldn't, IAM will notice it and stop them. If someone leaves the company, IAM quickly removes their access, so they can't get back in. This constant watching and adjusting is crucial. It helps make sure that the rules are always being followed, and that the 'iam pandoraaa ass' areas remain protected even as people's roles change or they leave the organization. It's a really dynamic system, always adapting, in a way, to what's happening.
IAM as a Digital Bouncer and Your 'iam pandoraaa ass' Guard
You can think of IAM as the ultimate digital bouncer at the door of a very exclusive club. This club, in our example, holds all of your company's important digital information. The bouncer, which is IAM, has a very long list. This list tells the bouncer exactly who is allowed in and what they are allowed to do once they are inside. If your name is on the list, and you have the right credentials, you get to enter. If not, you stay outside. It's that simple, really. This is how IAM acts as your 'iam pandoraaa ass' guard, making sure that only the approved individuals get near your most sensitive digital assets. It's a very straightforward way to manage who has permission to access your valuable stuff.
This bouncer role is not just about letting people in or keeping them out. It's also about making sure that once someone is inside, they stick to the rules. For example, the bouncer might let you into the main area of the club, but not into the VIP section unless you have a special pass. Similarly, IAM lets users into the general network, but restricts their access to specific applications or data sets based on their defined role. This layered approach helps protect different levels of information. It means that even if someone manages to get past one barrier, there are still other checks in place to keep your 'iam pandoraaa ass' areas safe. It's a pretty robust way to manage access, you know?
IAM is always checking and re-checking. It is like the bouncer constantly looking at the list, even after someone has entered, to make sure they are still authorized to be there and to do what they are doing. This continuous verification is what makes IAM so powerful in guarding against unwanted access. It helps stop hackers who try to pretend they are someone else, and it helps prevent mistakes or bad actions from people who are already inside the system. It is, in some respects, your company's personal digital security guard, keeping a very close watch over who, where, and when your company data is accessed. This constant vigilance is a very important part of keeping your 'iam pandoraaa ass' protected.
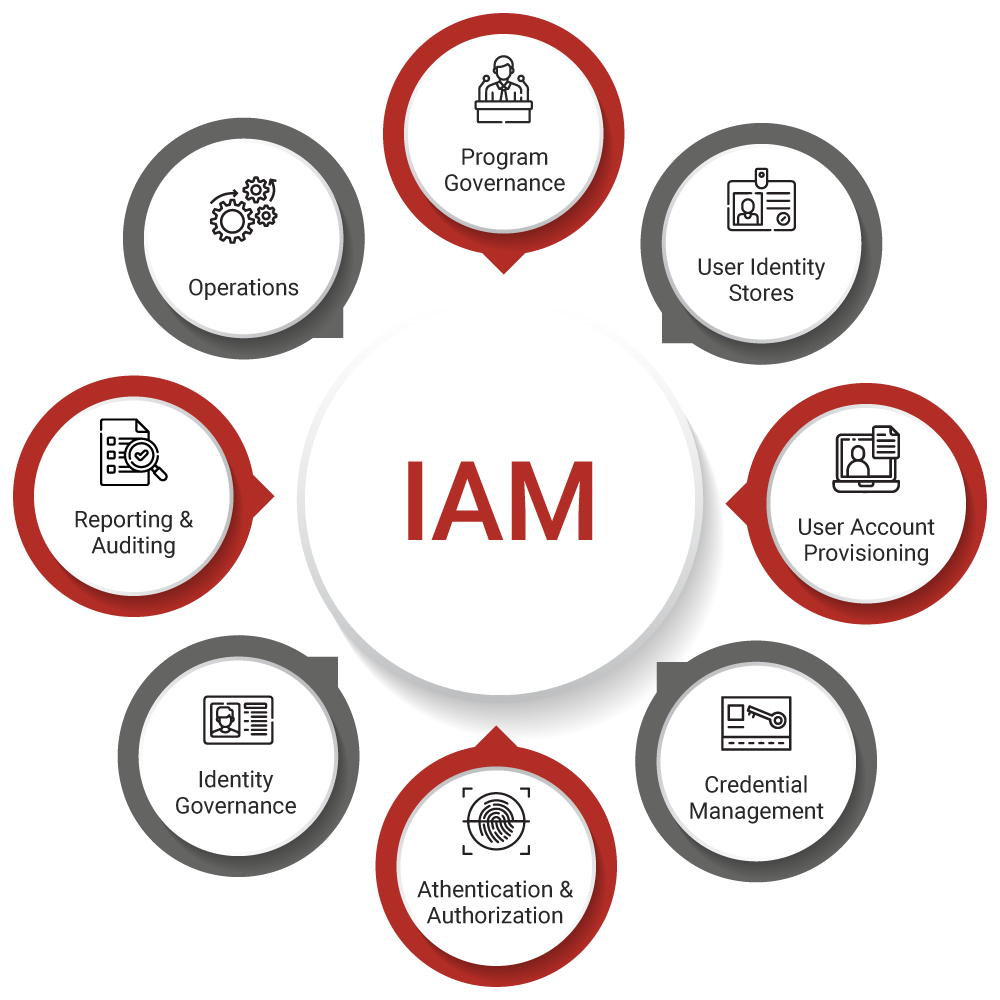
The Building Blocks of IAM
To really get how IAM works, it helps to look at its main parts, its building blocks, if you will. These parts work together to create the full system. The first big piece is "identity management" itself. This is all about creating and keeping track of each person's digital identity. It is like creating a unique profile for every user, with all their relevant details. This profile is what the system uses to recognize them. It includes things like their username, their role in the company, and any special permissions they might have. This is the foundation upon which everything else is built, really. It's how the system knows "who" someone is, which is a very basic but vital step.
Then there's "access management." This part takes those identities and decides what they can actually do. It's about setting up the specific rules for what resources a user can get to, and what actions they can perform. For example, a marketing person might have access to the company's social media accounts, but they wouldn't have access to the payroll system. This is where the concept of "least privilege" comes in, which means giving people only the minimum access they need to do their job, and nothing more. It's a pretty smart way to limit potential problems. This part of IAM is like giving out different sets of keys, where each key only opens certain doors, you know?
Another key piece is "authentication." This is the process of proving that someone is who they say they are. It's like showing your ID at the door. This can involve passwords, of course, but also things like fingerprint scans, face recognition, or special codes sent to your phone. These extra layers of checking make it much harder for unauthorized people to get in, even if they somehow get hold of a password. It adds a very strong lock to the digital door. Then there's "authorization," which happens after authentication. This is where the system checks what the authenticated user is *allowed* to do. It's the step where the bouncer checks the list to see which parts of the club you can enter. These two steps work hand in hand, actually, to keep things secure.
Keeping the Wrong Folks Out
A big part of what IAM does is simply keeping the wrong folks out. It's about building strong digital walls and making sure there are no easy ways for uninvited guests to get in. This means setting up very clear boundaries for who can access what. Think about it: if every employee had access to every single piece of company information, it would be a complete mess, and also very risky. IAM helps prevent this chaos by making sure that access is given out very carefully and only when it's truly needed. It's a bit like having a very strict policy on who gets a key to the safe, you know? Only those with a genuine need, and the right authorization, should have that kind of access.
This careful management of access is what helps stop hackers in their tracks. Hackers are always looking for weak spots, for open doors, or for ways to trick the system into thinking they are someone else. IAM makes those tricks much harder to pull off. By requiring strong authentication and by limiting what each user can do, even if a hacker gets one piece of information, they can't necessarily get to everything else. It's like having many small, locked compartments instead of one big, easily breakable box. This layered defense is very important in today's world, where digital threats are always popping up. It really helps keep the bad guys from getting their hands on your valuable stuff.
Beyond just stopping hackers, IAM also helps prevent simple mistakes. Sometimes, people accidentally click on the wrong link, or they try to access a file they shouldn't. With IAM in place, even if they make a mistake, the system will prevent them from doing something that could cause harm. It acts as a safety net, catching potential problems before they become real issues. This kind of prevention is very valuable, as it saves companies a lot of time and trouble down the line. It's about making the digital environment as safe and foolproof as possible for everyone who uses it, which is a pretty good goal, I think.
Making Sure IAM is Always On Watch
One of the really important things about IAM is that it is not a one-time setup. It's not something you just put in place and then forget about. IAM is always on watch, always monitoring, and always adapting. Think of it like a security guard who never takes a break, always patrolling the building and checking the doors. As people join the company, leave, or change roles, their access needs to be updated. IAM systems are designed to handle these changes smoothly and quickly. This continuous management makes sure that the right people always have the right access, and that no one has access they shouldn't, which is a very important part of ongoing security.
This constant vigilance includes keeping an eye on how people are using their access. IAM systems can log every time someone tries to get into a system, what they access, and what they do with it. This creates a clear record of activity. If something unusual happens, like someone trying to log in from a strange location, or trying to access a file they never usually touch, the IAM system can flag it. This kind of monitoring helps catch suspicious activity early, before it turns into a major problem. It's like having a detailed report of everyone's movements within the digital space, which can be very useful for spotting anything out of the ordinary, you know?
The ability of IAM to adapt and respond to new threats is also key. The world of digital security is always changing, with new types of attacks emerging all the time. A good IAM system can be updated and adjusted to deal with these new challenges. It's not a static defense; it's a living, breathing security framework that evolves with the threats. This means that your digital defenses remain strong and effective over time, even as the landscape of cybersecurity shifts. It really helps keep your valuable information protected against whatever new dangers might appear on the horizon. It's basically a proactive approach to keeping things safe, which is a very smart way to go about it.
The Big Picture of IAM and Your 'iam pandoraaa ass'
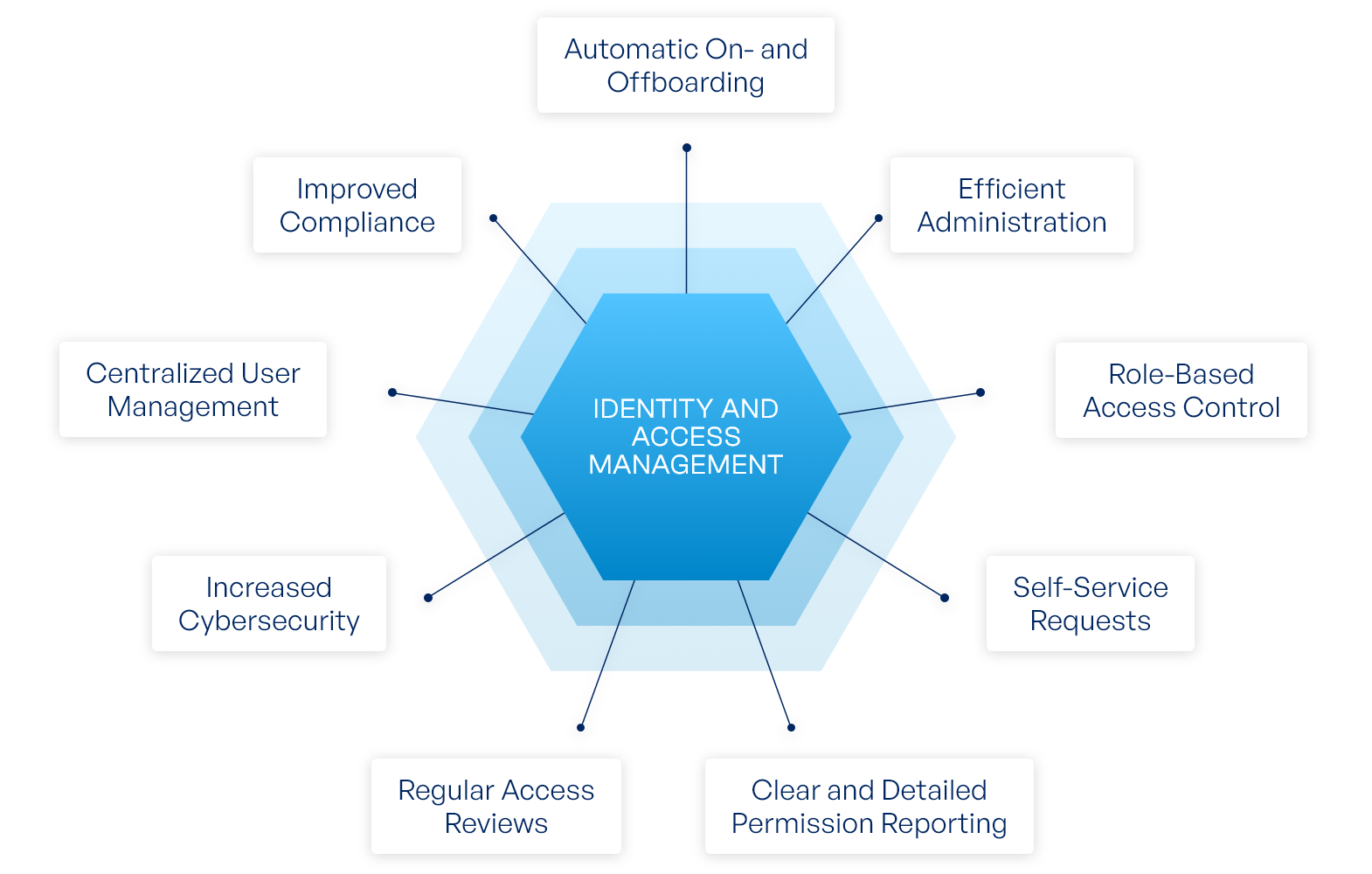
When we look at the big picture, IAM is a really important part of keeping any organization's digital life safe and sound. It's not just about stopping hackers; it's about creating an orderly, controlled environment where everyone can do their work securely. It helps companies manage their digital identities and control who gets to use critical company resources. This framework of policies, processes, and technologies works together to make sure that the right individuals have the right access at the right time, and that those sensitive 'iam pandoraaa ass' areas are always under guard. It's a very comprehensive way to approach digital security, covering many different angles, you know?
IAM plays a very big role in helping organizations protect themselves from a whole range of digital dangers. By carefully managing who can access what, it helps prevent data from falling into the wrong hands, whether those hands belong to an outside attacker or an insider who might make a mistake. It provides a clear way to tell who a user is and what they are allowed to do, which is the foundation of any good security system. It's like having a very clear rulebook for digital access, which everyone understands and follows. This clarity and control are what make IAM such a vital tool for any business today. It really simplifies a very complex problem, in a way.
Ultimately, IAM is about peace of mind. It's knowing that your company's valuable digital assets are being looked after with great care. It means that you can trust that only authorized people are getting to the information they need, and that your most sensitive data is shielded from harm. It's a fundamental part of cybersecurity that helps organizations stay safe, compliant with rules, and productive. So, when you think about protecting your 'iam pandoraaa ass' points, think of IAM as the dedicated, ever-present guardian making sure everything stays secure and exactly where it should be. It's a really essential piece of the puzzle for keeping things safe in our very connected world, actually.
This article has talked about what identity and access management (IAM) is, how it helps organizations secure, manage, and define roles and access for users, and why it's important. We covered how IAM is like a digital security guard, keeping watch over who, where, and when company data is accessed, and how it helps stop hackers and protects against insider threats and data breaches. We also looked at how IAM works as a framework of policies, processes, and technologies to manage digital identities and control user access to critical corporate resources, and how it acts like a bouncer at a nightclub, with a list of who is allowed to access what.
- Momos Bar Portland
- Cloud Smoke Shop Nutley
- Angel Wiley Age
- Seven Points Uptown
- Bronte London Restaurant
A Closer Look at Identity and Access Management (IAM) and Privileged
What Is Identity and Access Management? IAM Beginner's Guide
Identity and Access Management (IAM) overview | Okta Developer